In this increasingly sophisticated digital era, without realizing it, many frauds have occurred with various motives and are easy for us to believe. So that it is very dangerous for personal data, or also our privacy. That way we also have to study the motives of fraud that occur in an increasingly sophisticated digital era.
The following are examples of fraud and how to distinguish between genuine and fake in this fraud motive.
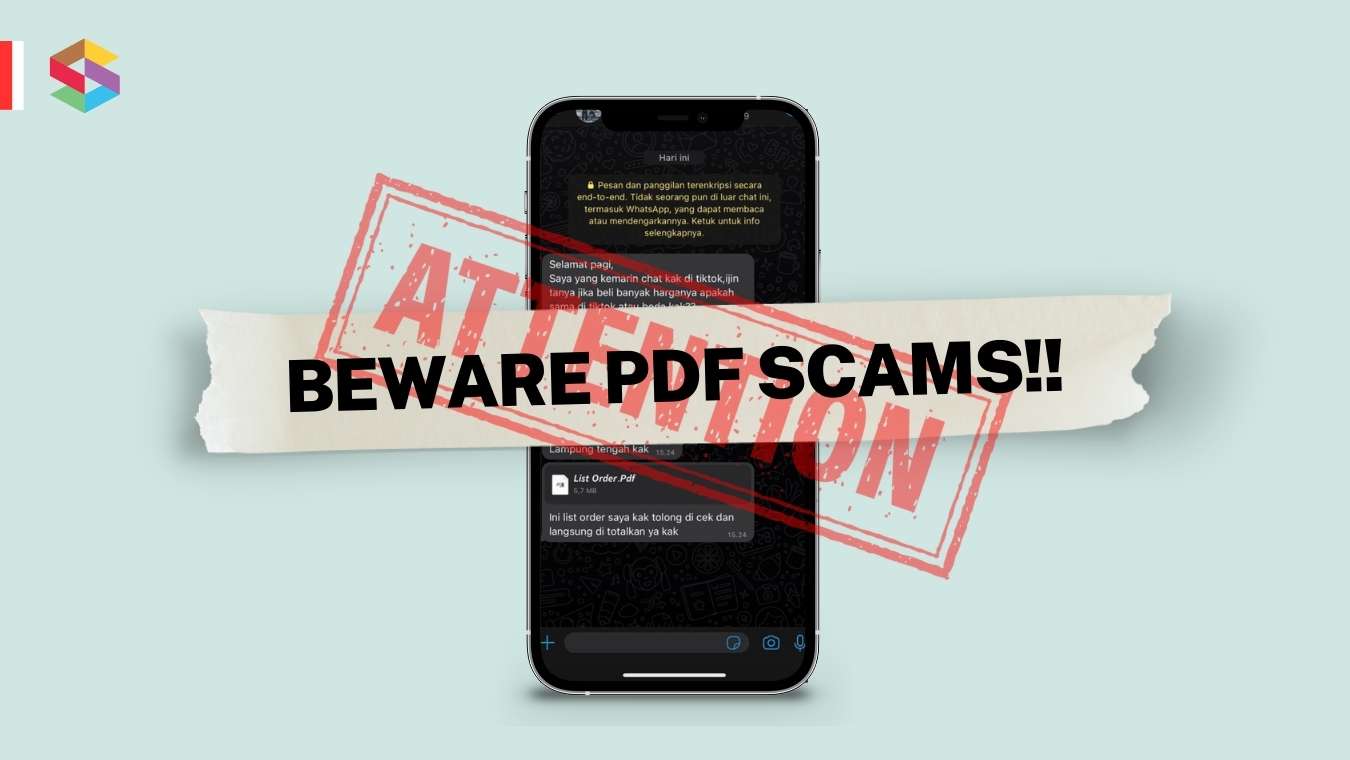
Usually, this fraud often occurs with people who use social media such as WhatsApp, which used to use the APK motif, now it is common to use PDF.For information, an APK file or Android Package Kit is a file format used to install software or applications on Android. Meanwhile, Portable Document Format or PDF is a file format that displays two-dimensional documents. By renaming or renaming the file using the ".pdf" suffix, the appearance of the file when sent will look like a PDF.However, cyber security expert from Vaccine, Alfons Tanujaya, denied that this method could distinguish genuine and fake PDF files. Based on experiments conducted by Alfons, APK files that are renamed with the addition ".PDF" or ".pdf" will also change their icon to PDF.
How to distinguish real and fake PDFs
Alfons continued, fortunately the WhatsApp system will verify the extension before running the file, and the file will be considered corrupt or damaged. For example, with a notification or notification in the form of :
1. "This document might contain unsafe content. Make sure you trust the sender before you open it." Or in Indonesian it means, "This document may contain unsafe content. Make sure you trust the sender before opening it."
2. "We can't show the file because it's corrupted." Or "We can't display the file because it's corrupt."
According to Alfons, instead of getting confused by distinguishing the original PDF or not, the easiest way is to deactivate all application installation permissions. As for the method, namely :
1. Go to "Settings" or "Settings" for each cellphone
2. Select "Install Unknown Apps" or "Install Unknown Apps"
3. Do not check or uncheck applications to refuse permission to install applications from unknown sources.
The following is an example of fraudulent motives that are rife today, and how can we distinguish between genuine data and fake data. Be careful if you reveal something you have nothing to do with or feel like you've never contacted that person.
source - Beware PDF Scams!!

 ENGLISH
ENGLISH INDONESIA
INDONESIA